How to Protect Your Business in the Evolving Cyber Threat Landscape with DrayTek
Are you being proactive about your network security?
Ransomware cyberattacks like WannaCry and NotPetya have dominated headlines the past few months. These attacks caused havoc worldwide by locking out thousands of users, encrypting their data and demanding ransom. However the vulnerabilities that these attacks targeted were not zero-day but could have been mitigated with basic security best practices such as regular Windows upgrades and backups.
Security breaches targeting confidential user data and core infrastructure services, have become increasingly common in recent years. Lost data might be recovered but customers' trust is not easy to regain. It takes years for a company to build a solid reputation, but only one security breach to destroy customer trust.
How much security is really enough? This question haunts every organization, but is especially crucial for small businesses with limited security budgets. The subscription based security solutions from most enterprise network manufacturers today can be too expensive or complicated to configure and require trained technicians and support contracts to be maintained. Similarly, home users wish to protect their families from the dangers of accessing harmful content on the Internet, but don't know where to begin.
Confidentiality, Integrity and Availability are the three pillars of IT security and Draytek provides a one-stop solution for your security dilemma. The need to incorporate secure practices in your network without compromising usability, has always presented a dilemma to administrators. DrayTek devices attempt to resolve this dilemma with several built-in security features that help you protect users while keeping your costs down.
Powerful Built-in Firewall
The firewall on the DrayTek routers forms the basis for all the other security features such as content security management and user management. It offers you complete control over the network traffic passing between your LAN and WAN networks.
All DrayTek routers have a Layer 3 packet filter which lets you filter traffic based on information in the packet header such as source and destination IP addresses, ports and protocols. They also have a Layer 7 application layer filter or CSM which does further inspection into the packet data to accept or deny packets based on their applications. E.g. block all peer-to-peer applications or all Social Media websites. All DrayTek routers offer four types of CSM:
- Application Enforcement: DrayTek routers offer a built-in Application Enforcement feature that inspects and recognizes the application in use by a client by comparing the traffic flow pattern to its database.
- URL Content Filter: If this feature is enabled, the firewall will inspect HTTP packets and check if the URL contains certain keywords specified by the network admin.
- Web Content Filter: This real-time service is provided by Cyren, a well known security leader that monitors and classifies millions of websites in real-time and is the only licensed service on your DrayTek router.
- DNS Filter: Acts as an extension to the URL and WCF filters to check the initial DNS queries to see if they contain any specified keywords or categories.
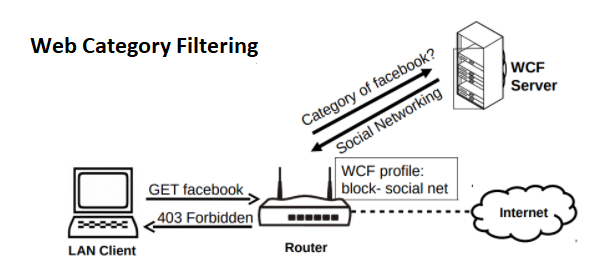
What does this mean for your network? You can pass or block traffic based on URL filters, Web Category Filters, Time Schedules, QoS policies, User Roles and Application Filters. With the WCF license, it’s simple and inexpensive to implement Child Protection rules for homes and schools campuses. The DNS Filter ensures that even HTTPS websites are also filtered correctly. APP Enforcement can filter applications such as Peer-to-Peer (P2P), Instant Messenger, Tunnel protocols, Remote Control protocols etc.
Denial-of-Service Defense:
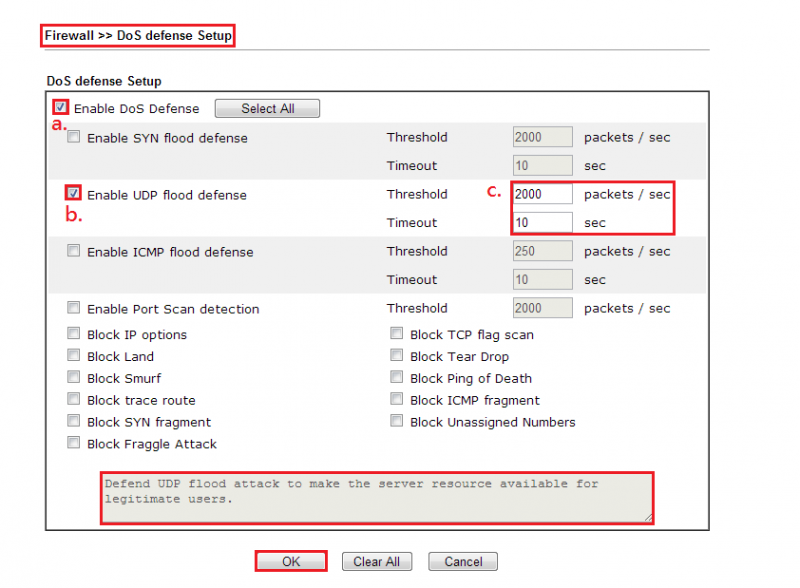
In Denial-of-service attacks, hackers use automated bots to flood the router with fake connection requests to make it unavailable for legitimate users. By enabling DoS Defense in DrayTek firewalls, router will block all connection requests from unknown sources after a certain specified threshold is reached for a certain timeout period. It will also generate alerts to notify the network admin that it is under attack and the responsible source IPs, so that further action can be taken.
Comprehensive VPN Support on DrayTek devices now includes IKEv2
Draytek Vigor routers provide multiple simultaneous VPN tunnels with support for secure protocols IPSec (IKEv1/IKEv2) and SSL for secure data exchange and communication.
With a dedicated VPN co-processor, hardware encryption is seamlessly handled, thus maintaining maximum router performance and throughput. This means our popular models are capable of supporting from 50 to 500 simultaneous VPNs with high IPSec throughput.
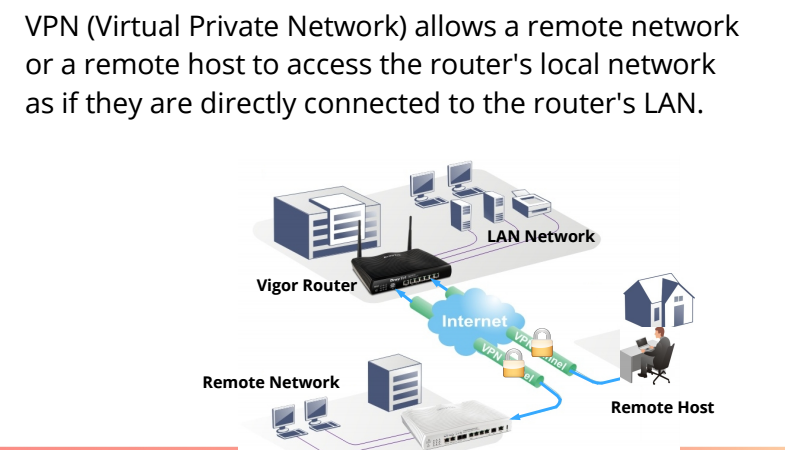
Moreover, DrayTek’s SmartVPN client which is available free of cost for Windows, Mac OS, Android and IPhones makes it easy for teleworkers securely connect to their office networks using SSL to access internal applications, remote desktops, file servers etc.
VPN Backup and Load-Balancing: In spite of the many advantages of using VPNs, many users are wary of them because of the single-point of failure they present, especially for inter-office connections. With the DrayTek VPN Backup feature you can maintain a permanent connection between two sites. Once a VPN connection drops, an automatic backup VPN connection will be implemented.
Wireless Security
Draytek routers and access points support industry accepted wireless security standards such as WPA2 and AES. They also support 802.1X for centralized wireless security management utilizing dynamic single-session, single-user encryption keys integrated with network log-on with the help of a RADIUS server.
This dramatically simplifies the administration and management of the network by eliminating the deficiencies of static key management, giving IT managers the confidence to deploy a secure enterprise-wide wireless solution for their users. Access control with MAC address stops unauthorized clients from accessing your wireless network. Also included is the ability to hide your SSID, Isolate Wi-Fi clients from wired LAN network and Isolate Wi-Fi users from each other.







