How to Protect your IP PBX with DrayTek firewalls
It is very common to open ports on the router so that select internal services are reachable from the Internet. For example, you might wish to open port 5060 for SIP traffic and a range of UDP ports for RTP traffic in the router, and redirect to your internal PBX. However opening ports without any restrictions can expose your network to malicious activity. It's suggested that you restrict access to open ports to a list of pre-approved source IP addresses on the Internet.
Open Ports: Convenience vs. Security Risk
Here is how you can restrict access to open SIP port 5060, to an approved source IP address on the Internet e.g. 100.100.100.1 only.
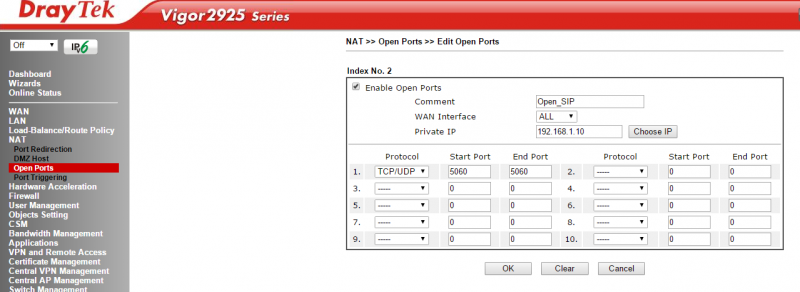
1> Forward port 5060 to your internal IP address (e.g. 192.168.10.1) under NAT->Open Ports
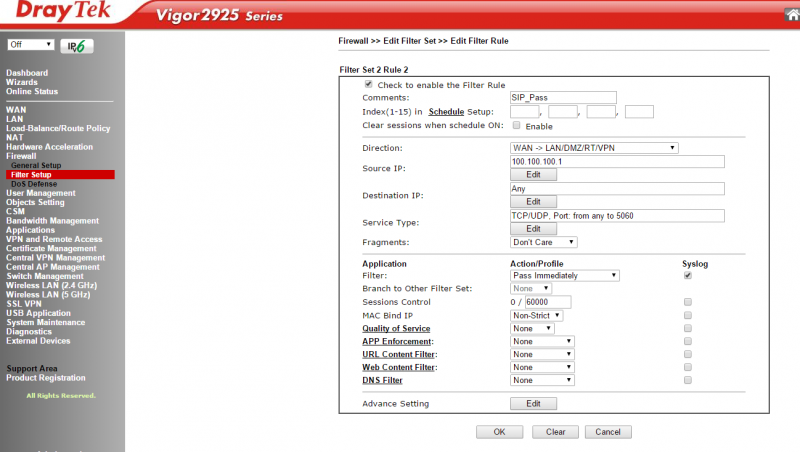
2> To restrict access, you will need to setup two firewall policies under Firewall->Filter Setup->Default Data Filter.
3> First policy will allow WAN->LAN traffic to port 5060 from your allowed list of source IP addresses e.g. 100.100.100.1.
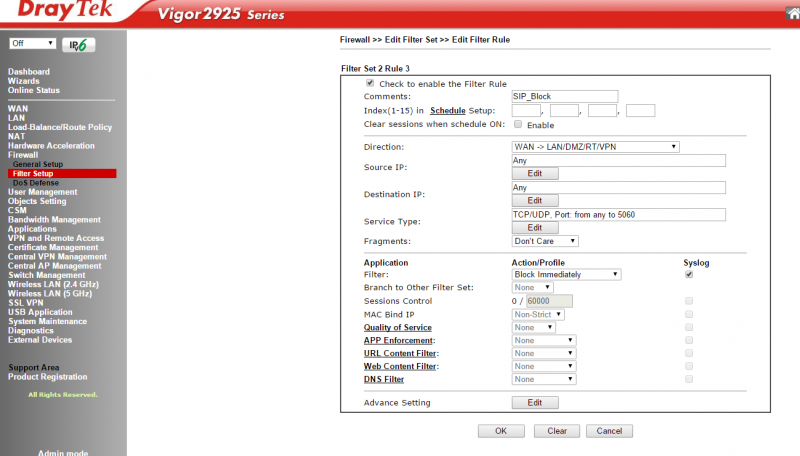
4> Below it, you need another policy to block all WAN->LAN traffic to port 5060, no need to specify source IP addresses here.
Restricting Port Access: Securing Your Network
The firewall will check the source IP address against the first policy and pass traffic if it matches your allowed list. If not, then it will block all traffic to port 5060 from unathorized source IP addresses. So the order of the policies is important.
If you select syslog for both the policies, you can see the action the firewall takes for each session under Diagnostics->Syslog Explorer.







